Module 4
It's a difficult module in this series, Using PowerShell for Active Directory. In this module, Jason and Ashley talked about forensic investigations and lockout in Active Directory. They used many PowerShell to do demonstrations.
First of all, Ashley used .Net code, [System.Security.Principal.SecurityIdentifier] to work with PowerShell to get Enterprise Admins, Domain Admins. The scripts are the following:
$SID_GROUP_EA = [System.Security.Principal.SecurityIdentifier]"$((Get-ADDomain -Identity (Get-ADForest).Name).DomainSID)-519"
$SID_GROUP_DA = [System.Security.Principal.SecurityIdentifier]"$((Get-ADDomain).DomainSID)-512"
$SID_GROUP_AD = [System.Security.Principal.SecurityIdentifier]'S-1-5-32-544'
$SID_USER_AD = [System.Security.Principal.SecurityIdentifier]"$((Get-ADDomain).DomainSID)-500"
Get-ADGroup $SID_GROUP_EA -Properties * -Server (Get-ADForest).Name
Get-ADGroup $SID_GROUP_DA -Properties *
Get-ADGroup $SID_GROUP_AD -Properties *
Get-ADUser $SID_USER_AD -Properties *
Then, they talked about "Get-ADReplicationAttributeMetadata" to get metadata like last change from which domain controller, version, attribute name and so on. They explained the usage of some attribute names. "Get-ADReplicationAttributeMetadata" with the parameter, -ShowAllLinkedValues" can get the group history of user accounts which are joined.
Get-ADUser $userobj.DistinguishedName -Properties memberOf |
Select-Object -ExpandProperty memberOf |
ForEach-Object {
Get-ADReplicationAttributeMetadata $_ -Server localhost -ShowAllLinkedValues |
Where-Object {$_.AttributeName -eq 'member' -and
$_.AttributeValue -eq $userobj.DistinguishedName} |
Select-Object FirstOriginatingCreateTime, Object, AttributeValue
} | Sort-Object FirstOriginatingCreateTime -Descending | Out-GridView
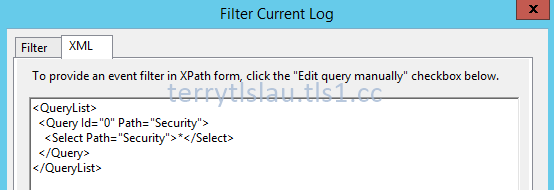
After that, they talked about XML view of Event Logs. We can use "Filter Current Log" option to get the custom XML code of event log and then paste it to PowerShell to write our own scripts to get event from all domain controllers.
In Windows Server 2012 or later, we can perform "Search-AdAccount -LockedOut" to find which accounts were locked.
Finally, they performed a lot of scripts to check permissions of Active Directory.
Remark: All PowerShell scripts were written by Ashley McGlone. You can download the scripts from the following web site.
For more information:
Related posts:
This posting is provided “AS IS” with no warranties, and confers no rights!

No comments:
Post a Comment