Cluster FQDN: cs01.contoso.com
Computer FQDN: Ex02.contoso.com
Redundant Computer FQDN: Ex02rep.contoso.com
Roles: CCR Active Mailbox Server
Operating System: Windows Server 2008 R2 Enterprise
Network: 172.16.2.2 (Public), 172.16.2.12 (Redundant)
Computer FQDN: Ex03.contoso.com
Redundant Computer FQDN: Ex03rep.contoso.com
Roles: CCR Passive Mailbox Server
Operating System: Windows Server 2008 R2 Enterprise
Network: 172.16.2.3 (Public), 172.16.2.13 (Redundant)
When I try to enable the redundant cluster network of Cluster Continuous Replication in Windows Server 2008 R2, I found the following error:
The addition host names cannot work. However, the resource groups were added in Failover Cluster Manager.
I read the article from the following link to solve my problem:
When the replication service first starts up <or> the configuration time expires the replication service enumerates all network names on the cluster to determine which are valid endpoints for log shipping. This is initially based on two cluster private properties stamped on each name, MSExchange_NetName and MSExchange_UseNetworkForLogCopying. Each of these should have a value of 1 on a network name utilized as a continuous replication host name.
On the surface it would appear that there is nothing preventing this name from operating correctly as a continuous replication host name. After performing some internal tracing it was determined that the replication service is also implementing another check on a network name resource to ensure that it can be satisfactorily utilized for replication – is Kerberos enabled for the network name. The replication service performs this check by reviewing a private property of a network name resource – requirekerberos and ensuring it has a value of 1.
In Windows 2003 network name resources could be enabled for Kerberos at the administrators discretion. In Windows 2008 and Windows 2008 R2 all network names must be Kerberos enabled. In Windows 2008 requireKerberos is a valid private property and can be programatically set. In Windows 2008 R2 the requireKerberos property has been deprecated and can be no longer be programmatically set. Without the requireKerberos property in Windows 2008 R2 the enable-continuousreplicationhostname commandlet fails with the previously documented error.
To work around this issue and allow the replication host names created with the enable-continuousreplicationhostname command to function the following steps can be performed:
1. Using the Exchange Management Shell invokes the enable-continuousreplicationhostname cmdlet. Allow the command to create the resource group, network name and IPv4 resource.
2. Verify with Failover Cluster Manager that the resource group, network name and IPv4 resource were created and are online.
3. Manually set requireKerberos utilizing either cluster.exe or Failover Cluster PowerShell extensions (preferred)
Cluster.exe
1. At EX02, log in as Domain Administrator.
2. Launch "Command Prompt", enter the following commands to add "requirekerberos" parameter:
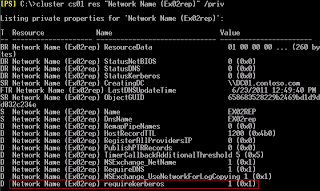
cluster cs01 res "Network Name (Ex02rep)" /prive requirekerberos=1:DWORD
cluster cs01 res "Network Name (Ex03rep)" /prive requirekerberos=1:DWORD
Remark: "requirekerberos" is all lowercase.
cluster cs01 group "Ex02rep_group" /offline
cluster cs01 group "Ex03rep_group" /offline
cluster cs01 group "Ex02rep_group" /online
cluster cs01 group "Ex03rep_group" /online
5. Enter the following commands to restart the Microsoft Exchange replication service:
net stop msexchangerepl
net start msexchangerepl
net stop msexchangerepl
net start msexchangerepl
Remark: You have to restart the Microsoft Exchange replication service in both servers.
PowerShell
1. At EX02, log in as Domain Administrator.
2. Launch "PowerShell", enter the following cmdlet to import failover cluster powershell extension:
Import-Module FailoverClusters
Get-ClusterResource "Network Name (Ex02rep)" | Set-ClusterParameter -Create requirekerberos 1Get-ClusterResource "Network Name (Ex03rep)" | Set-ClusterParameter -Create requirekerberos 1
Remark: "requirekerberos" is all lowercase.
4. Enter the following cmdlets to take the continuous replication hostname groups offline:
Stop-ClusterGroup -Cluster cs01 -Name Ex02rep_group
Stop-ClusterGroup -Cluster cs01 -Name Ex03rep_group
5. Enter the following cmdlets to take the continuous replication hostname groups online:
Start-ClusterGroup -Cluster cs01 -Name Ex02rep_group
Start-ClusterGroup -Cluster cs01 -Name Ex03rep_group
6. Enter the following cmdlet to restart the Microsoft Exchange replication service:
Restart-Service msexchangerepl
Remark: You have to restart the Microsoft Exchange replication service in both servers.
At this time you can utilize either cluster.exe or powershell to verify that the requirekerboros key has been created with a value of 1.
Command
Cluster cs01 res "Network Name (Ex02rep)" /priv
Cmdlet
Get-ClusterResource "Network Name (Ex02rep)" | Get-ClusterParameter
As a result, the redundant host names of CCR were added.
RequireKerberos Reference:
http://technet.microsoft.com/en-us/library/cc772544(WS.10).aspx
This posting is provided “AS IS” with no warranties, and confers no rights!
This posting is provided “AS IS” with no warranties, and confers no rights!